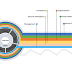
Traditional WAN vs SD-WAN solutions
ohhhvictor
June 21, 2023
1. Traditional WAN : Traditional network is based on completely hardware network devices which mostly rely on Multi Protocol Label Switc...Read More
Traditional WAN vs SD-WAN solutions
 Reviewed by ohhhvictor
on
June 21, 2023
Rating:
Reviewed by ohhhvictor
on
June 21, 2023
Rating:
 Reviewed by ohhhvictor
on
June 21, 2023
Rating:
Reviewed by ohhhvictor
on
June 21, 2023
Rating: