Wireless technology
Wireless technology
WLAN frequency ranges are in the 2.4GHz and 5GHZ bands. The most common legacy wireless standards, 802.11b and 802.11g, use the 2.4GHz range. IEEE 802.11a uses 5GHz exclusively. The newer 802.11n operates mostly in 5GHz but can also use the 2.4GHz band.
- Hertz (Hz) = One hertz is equal to one cycle per second.
- Cycle = One complete wave
- Wireless bands = subdivides into channels
A milliwatt is somewhat the opposite of a kilowatt, being a thousandth of a watt, represented as mW when written. The mW is going to be your second most popular unit of power, with most APs both IoT and Wi-Fi, emitting between 1 mW and 1 full watt, usually constrained by regulatory agencies rather than the capability of the device itself.
mW being the second most popular measure you'll run into; the other is dB or dBm. Decibels (dB) are a ratio measurement.
dBm is unlike RSSI as it is an absolute number representing power levels in milliwatts. RSSI is only a relative index of power.
Example:
The higher the ratio, the better the signal quality. For example, a Wi-Fi signal with S/N of 40 dB will deliver better network services than a signal with S/N of 20 dB.
We can use two access point modes of operations in wireless network deployment, Autonomous Access Point and Lightweight Access Point (LAP).
Autonomous AP Access Point
Autonomous APs work as standalone devices with no knowledge of other Access Points (APs). Moreover, Autonomous APs are managed individually unless a management platform, such as Cisco DNA Center and Cisco Prime Infrastructure, is used in the network.
Unlike Lightweight Access Point (LAP), which requires a Wireless LAN Controller (WLC), Autonomous Access Points don’t need Wireless LAN Controllers to function. It is independent and standalone, which is suitable to use for small networks.
Unlike Autonomous Access Points, Cisco Lightweight Access Points need Wireless Lan Controllers (WLC) to function fully. LAP and WLC form a CAPWAP tunnel that carries control and data traffic.
Control and Provisioning of Wireless Access Points (CAPWAP) is a standard and interoperable protocol that enables a Wireless LAN Controller (WLC) to manage access points (AP) or wireless termination points (WTP). CAPWAP is based on the Lightweight Access Point Protocol (LWAPP). This topic describes the changes in controller and AP software to enable CAPWAP support and to enable an upgrade from LWAPP to CAPWAP
The CAPWAP protocol does not include specific wireless technologies; instead, it relies on a binding specification to extend the technology to a particular wireless technology.

DTLS Encryption
DTLS is a protocol that provides security between the AP and the WLC. It allows them to communicate using encryption and prevents eavesdropping or tampering.
DTLS is enabled by default to secure the CAPWAP control channel but is disabled by default for the data channel, as shown in the figure. All CAPWAP management and control traffic exchanged between an AP and WLC is encrypted and secured by default to provide control plane privacy and prevent Man-In-the-Middle (MITM) attacks.
Cisco wireless AP modes
Local
Local mode is the default mode; it offers a BSS on a specific channel. When the AP doesn’t transmit wireless client frame, it’s still doing something behind the scenes. The AP scans other channels to:
- Measure noise
- Measure interference
- Discover rogue devices
- Check for matches against IDS events
Monitor
An AP in monitor mode doesn’t transmit at all. It’s a dedicated sensor that:
- Checks Intrusion Detection System (IDS) events
- Detects rogue APs
- Determines the position of wireless stations
Because the AP is only in monitor mode, it won’t broadcast an SSID so clients are unable to connect to the AP.
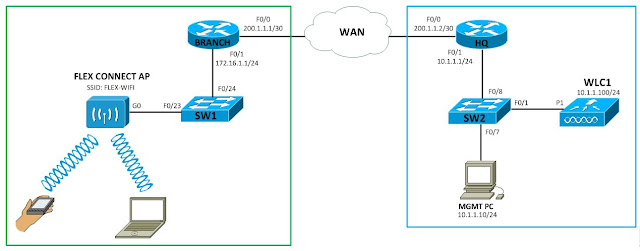
FlexConnect
It’s possible to connect a local mode AP at a remote branch to the HQ’s WLC. This works, but it’s not a good idea. First of all, the AP encapsulates all wireless client data through the CAPWAP tunnel over the WAN link. Secondly, when the WAN link is down, your wireless network at the branch site is offline too.
FlexConnect is an AP mode for situations like the one above. The AP can locally switch traffic between a VLAN and SSID when the CAPWAP tunnel to the WLC is down.
Sniffer
An AP in sniffer mode dedicates its time to receive 802.11 wireless frames. The AP becomes a remote wireless sniffer; you can connect to it from your PC with an application like Wildpackets Omnipeek or Wireshark. This can be useful if you want to troubleshoot a problem and you can’t be on-site. When an AP is in sniffer mode, it won’t broadcast an SSID so clients can’t connect to the AP.
Rogue Detector
Rogue detector mode makes the AP detect rogue devices full-time. The AP checks for MAC addresses it sees in the air and on the wired network. When the AP is in rogue detector mode, it can switch between rogue detection and serving clients. The AP can still broadcast an SSID and clients can connect to the AP.
Bridge/Mesh
The AP becomes a dedicated point-to-point or point-to-multipoint bridge. Two APs in bridge mode can connect two remote sites. Multiple APs can also form an indoor or outdoor mesh. You can’t connect to the bridge with clients.
Omnidirectional Antennas
Omnidirectional Antennas are antennas that pick up signals in all (or omni) directions, rather than just in one direction.
Directional Antennas
Dipole Directional antennas, on the other hand, only point their power in one direction. Because of this concentrated focus of dipole directional power, it has a greater signal range, allowing the antenna to pick up signals from much further away.
WLC Discovery process
- Broadcast on the local subnet.The CAPWAP AP sends broadcast discovery requests on the local subnet
- Local NVRAM list of the previously joined controller, Locally store WLC management IP address
- DHCP Option 43 returned from the DHCP server
- DNS lookup for “CISCO-CAPWAP-CONTROLLER.localdomain“
- if no controller would be found, LAP would reboot again, and go to discovery process again
Layer 2 and layer 3 roaming
Inter Controller-L2 Roaming : Inter-Controller (normally layer 2) roaming occurs when a client roams between two APs registered to two different controllers, where each controller has an interface in the client subnet.
 Reviewed by ohhhvictor
on
August 31, 2022
Rating:
Reviewed by ohhhvictor
on
August 31, 2022
Rating:
























No comments: