We can have a virtual path in a physical router, In the same way, we can virtualize VM server inside a physical server, we can virtualize routers inside physical routers.That is called VRF
Virtual routing and forwarding (VRF)
IP technology allows users to configure multiple routing table instances to simultaneously co-exist within the same router. Overlapping IP addresses can be used without conflict because the multiple routing instances are independent, and can select different outgoing interfaces.
VRFs are used for network isolation/virtualization at Layer 3 of the OSI model as VLANs serve similarly at Layer 2. Typically, users implement VRFs primarily to separate network traffic and more efficiently use network routers. Virtual routing and forwarding can also create VPN tunnels to be solely dedicated to a single network or client.
Types of VRF
Full VRF focuses on labeling Layer 3 traffic via MPLS—a similar idea to Layer 2 VLANS. The multiprotocol label switching or MPLS cloud in the service provider cloud environment uses multiprotocol border gateway protocol, or MP BGP. VRF isolates traffic from source to destination through that MPLS cloud. To separate overlapping routes and make use of common services, VRF incorporates Route Distinguishers (RDs) and Route Targets (RTs).
VRF lite, actually a subset of VRF, is normally VRF without MPLS and MP BGP. VRF lite is generally used in the office LAN or data center environment to virtualize various security zones and network elements.
Full VRF is a highly scalable solution, whereas VRF lite is not scalable.
You can even assign 2 similar ip addresses to different devices if they belong to different routers, and they are logically separated, and different network
Virtual routing and forwarding provides a path to configuring multiple routing instances on either a router or layer 3 switch. The purpose is to keep customer traffic and routing separate but through the same hardware.
In cases when VRF can't be used, customer traffic is routed using physical interfaces or subinterfaces with access control list -based filtering dividing the traffic. For this reason, VRF has gained popularity with corporate local area networks (LANS), data center and service providers using Multiprotocol Label Switching (MPLS) and Multiprotocol BGP (MP-BGP).
VRF uses the same methods of virtualization as virtual LANs (VLAN). They are equivalent to the Layer 3 version of a TCP layer of a VLAN. Because both routing instances operate independently, they can use the same ip address without any friction.
The network works better in this way because network paths can be segmented without needing multiple routers to do so. Also, VLAN can make a single switches a multi-switch, whereas VRF can make a single router appear to be multiple routes
We can have a default VRF using a loopback.
You can leak routes from default VRF to specific VRF
Route targets
Route targets are used to indicate which VRFs a VPN prefix should be imported into.
The “original” BGP would actually just overwrite one customer’s prefix with another customer’s prefix, because as far as BGP is concerned, they’re the exact same address. For all the receiver knows, the route target could have just changed, and the 2nd prefix is just a newer version of the 1st prefix.
we will use route target by VRF lite to limit the routes it exchange, specifically BGP routes between the default VRF and the VRF we just created
Site to site VPN
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network.
GRE Tunnels are very common amongst VPN implementations thanks to their simplicity and ease of configuration. With broadcasting and multicasting support, as opposed to pure IPSec VPNs they tend to be the number one engineers’ choice, especially when routing protocols are used amongst sites but still are not preferred to use very frequently.
GRE creates a virtual tunnel interface, so any packet that would be routed out this interface will be completely wrapped into a new packet.t.
IPSec on the other hand is a suite of protocols with a goal: to enforce a policy. IPSec does not really support multicast in and of itself. Now there are ways around this. For example, we might decide that we wish to encrypt the GRE packet that we created above. In that case, we might add an ESP header in the above mix. In that case, multicast would still work, but we are only encrypting a unicast packet from the perspective of IPSEC (or more specifically the ESP protocol).
IPsec provides more comprehensive security for IP tunneling, while GRE tunnels work well when network teams need to tunnel with multiple protocols or multicast. Generic Routing Encapsulation, or GRE, and IPsec both encase packets, but the two protocols have different requirements...
GRE – A GRE tunnel is used when IP packets need to be sent from one network to another, without being parsed or treated like IP packets by any intervening routers.It s very flexible
IPSec – IPsec ESP is used when IP packets need to be exchanged between two systems while being protected against eavesdropping or modification along the way.It got a hashing algorithmic and encryption, and as it name implies, its more secure.It can only encapsulate only unicast packet.No broadcast or multicast
IPsec have two mode: 1.- transport mode: Use original header
2.- tunnel mode: encapsulate the entire packet
GRE over IPsec
IPsec cannot encapsulate multicast, broadcast, or non-IP packets, and GRE cannot authenticate and encrypt packets. By means of the GRE over IPsec technology, multicast and broadcast packets can be encapsulated using GRE and then encrypted using IPsec.
At the same time, a GRE-capable interface collects statistics about the volume of the traffic that has been encrypted and decrypted. When gateways are interconnected in GRE over IPsec mode, the gateways encapsulate packets using GRE and then IPsec.
LAB with GRE over IP sec using GNS3
we will assume that R2 and R3 are 2 ISP providers
Creating GRE tunnel
1.- we will replicate this topology
2.-Configuration in R1: similar in all switches
2.-Verification in R2: similar in all switches
3.-Creation of GRE tunnel
int tunnel 1
ip address 192.168.0.2 255.255.255.252
ip mtu 1400
ip tcp adjust-mss 1360
exit
this is on R1..do the same with values for R4 on its ip address
4.-Creating source and destination
int tunnel 1
tunnel source fa 1/0
tunnel destination 192.51.100.2
end
this is on R4..do the same with values for R1 on its ip address:
5.- Verify
Creating GRE tunnel
1.-Step 1
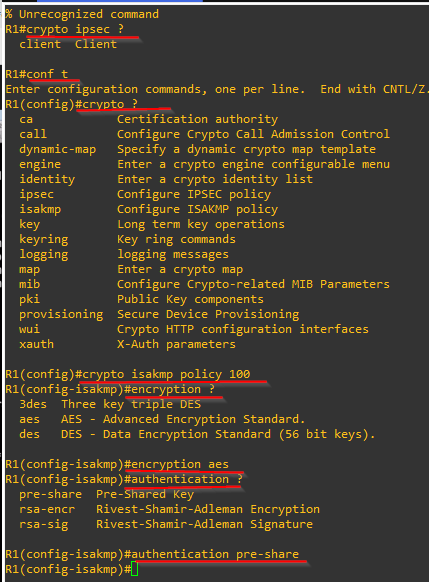
crypto ?
crypto isakmp policy 100
encryption aes?
encryption aes
authentication pre-share
group ?
group 2
exit
crypto isakmp key FloridaKey address 0.0.0.0 0.0.0.0
crypto ipsec transform-set MiamiHeat esp-aes?
crypto ipsec transform-set MiamiHeat esp-aes esp-sha-hmac
mode transform-set
exit
ip access-list extended GRE-IN_IPSEC
mat
pre
permit gre any any
exit
crypto map vpn ?
crypto map vpn 1000 ?
crypto map vpn 1000 ipsec-isakmp
mtach address GRE-IN_IPSEC
set transform-set MiamiHeat
set peer 198.51.100.2
exit
int fa1/0
crypto map vpn
3.-we can choose transport or tunnel mode. we will choosee transport4.-Acces list
5.-End configuration on R1
6.-We Will not repeat the same steps on R4 in this specific lab. Please try to do the same on R4 so you can understand and see all the processes.
In this lab, we could see the message that R1 is waiting for R4 to be configured and the crypto tunnel was made on R1.So the configuration on R1 is done!
Now simply change the same values to R4
Last steps on R4:
A.-Repeat the same steps on R4
B-Ping Lo of R4 (4.4.4.4)
C.-show crypto isakamp sa (confirm fase 1 on R4)
D.-show crypto ipsec sa (confirm fase 2 on R4)
I hope that you enjou and verify the lab .If it was useful, you did , please give me a "like"

 Reviewed by ohhhvictor
on
August 21, 2022
Rating:
Reviewed by ohhhvictor
on
August 21, 2022
Rating:




























No comments: