Wireless security
Wireless security is in essence, the prevention of unwanted users from accessing a particular wireless network. More so, wireless security, also known as Wi-Fi security, aims to ensure that your data remains only accessible to users you authorize.
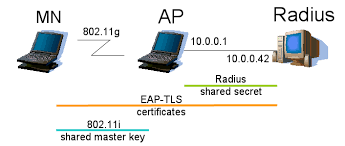
Extensible Authentication Protocol (EAP) is an authentication framework, not a specific authentication mechanism, frequently used in wireless networks and point-to-point connections. It provides some common functions and negotiation of authentication methods called EAP methods.
The EAP protocol can support multiple authentication mechanisms without having to pre-negotiate a particular one. There are currently about 40 different methods defined.
802.1X authentication involves three parties: a supplicant, an authenticator, and an authentication server.
- The supplicant is a client device (such as a laptop) that wishes to attach to the LAN/WLAN.
- The authenticator is a network device which provides a data link between the client and the network and can allow or block network traffic between the two, such as an switch,a wireless controller or access point.
- The authentication server is a trusted server that receive and respond to requests for network access, and can decide if the connection is to be allowed or not.
Remember: EAP is always carried by another protocol.The most common transports between the supplicant and the authenticator is EAPOL. EAP is transported over RADIUS
Native EAP (nontunneled EAP): EAP-TLS, EAP-MD5.
- EAP-TLS: An EAP type that uses TLS (Transport Layer Security) to provide the secure identity transaction. This is very similar to SSL and the way encryption is formed between your web browser and a secure website. EAP-TLS has the benefit of being an open IETF standard, and is considered "universally supported." t EAP-TLS is the most secure EAP type to use, since it is X.509 certificate-based authentication., where the client must trust the server’s certificate, and vice-versa. It is considered among the most secure EAP Types, since password capture is not an option; the endpoint must still have the private-key. Prefered EAP type of choice when supporting BYOD in the Enterprise.
- EAP-MD5: Uses a “Message Digest algorithm” to hide the credentials in a HASH. The HASH is sent to the server where it is compared to a local hash to see if the credentials were accurate.
However, EAP-MD5 does not have a mechanism for mutual authentication. That means the server is validating the client, but the client does not authenticate the Server (i.e.: does not check to see if it should trust the server). EAP-MD5 is common on IP Phones
- EAP MSCHAPV2 is an EAP version of the common MSCHAPV2 authentication mechanism. It provides mutual authentication between client and server. It is most commonly used as the inner authentication protocol with EAP PEAP on Microsoft Windows clients. EAP MSCHAPV2 does support dynamic WEP keys.It can be used with any Radiator AuthBy that has access to plaintext passwords
Tunneled EAP Types
The EAP types above transmit their credentials immediately. These next two EAP types form encrypted tunnels first and then transmit the credentials within the tunnel.
- PEAP: Protected EAP. this EAP Tunnel type ,the most popular in the world. PEAP will form a potentially encrypted TLS tunnel between the client and server, using the x.509 certificate on the server in much the same way the SSL tunnel is established between a web browser and a secure website.Proposed by Microsoft
- EAP-FAST: Flexible Authentication via Secure Tunnel (FAST) is very similar to PEAP. FAST was created by Cisco Systems as an alternative to PEAP that allows for faster re-authentications and supports faster wireless roaming.Use Protected Access Credentials(PAC)
- If this article was useful, , please click "like"bottom 😊
 Reviewed by ohhhvictor
on
September 15, 2022
Rating:
Reviewed by ohhhvictor
on
September 15, 2022
Rating:




















No comments: